A friendly reminder stay vigilant against scam emails from criminals and ne'er-do-wells
Criminals gonna crim. It's what they do. Sometimes its kids operating out of suburban basements. Sometimes it's a more professional outfit.
The trick isn't in stealing your money or assets - it's getting you to hand it over willingly - usually by logging into a fake account page using your real credentials - thus revealing them to the attacker.
Here at Linux Impact, we're used to all kinds of attempts to trick us into to handing over the keys to our email, our bank accounts, or even this very website.
We've not been fooled yet, but some attempts are better than others.
Here's one a look at one that could have worked...
The best scam emails are ones that you're expecting
If you routinely receive a lot of emails from a particular source, one more is likely to slip through unnoticed.
Check the WHOIS entry for this website, and you'll see that the very first Domain Profile entry is the name of the registrar. We bought this domain through NameCheap. It's super-easy for an attacker to find this, and it's also super-easy to craft an email purporting to be from the company.
As with many site owners, we have dozens of domain names registered, so receive emails from NameCheap multiple times per month.
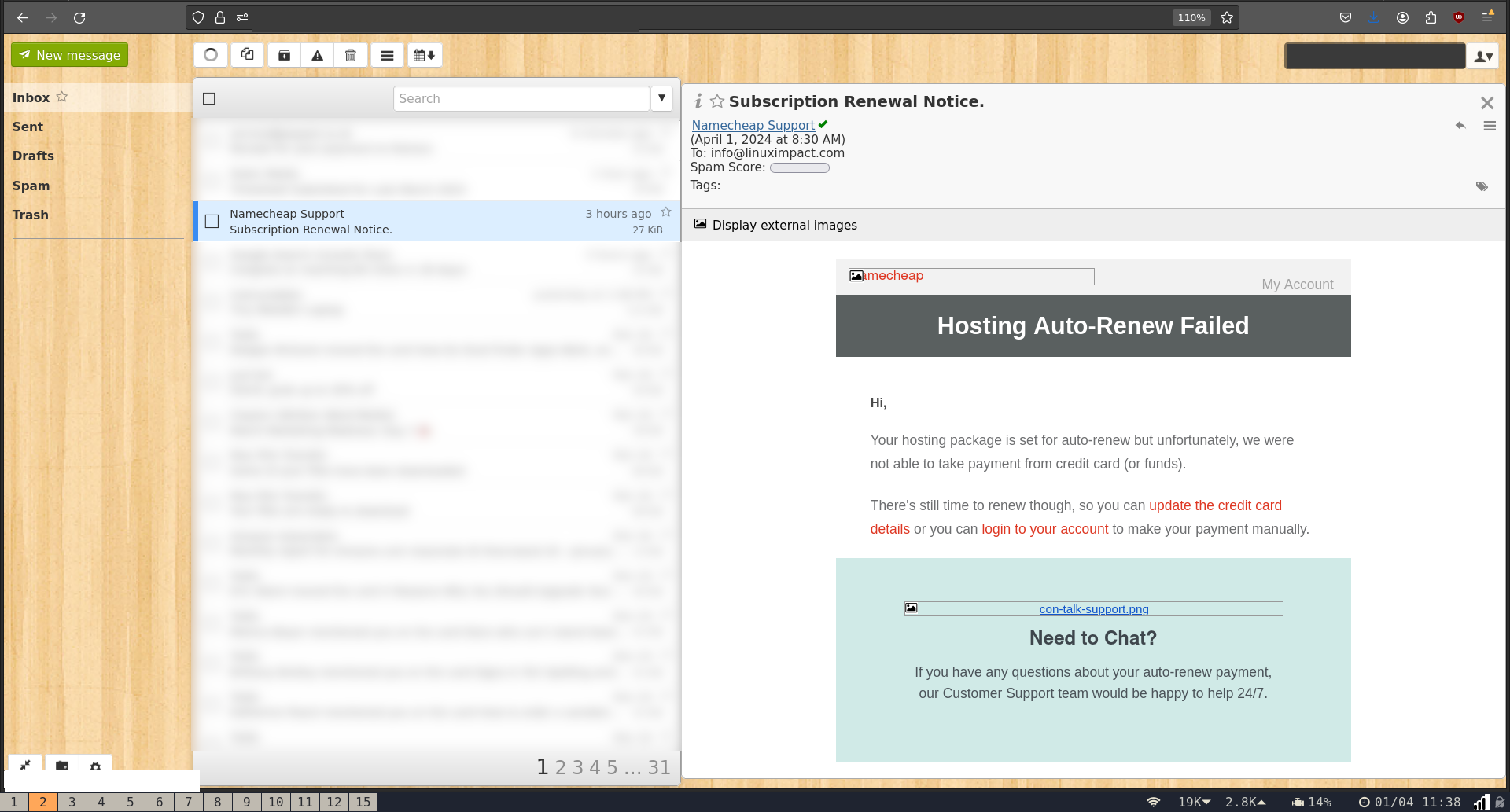
At first glance, the email seemed genuine. The from field read "Namecheap Support," and the subject was, "Subscription Renewal Notice."
It landed in our main inbox and wasn't flagged as spam. It wasn't attempting to spoof the Linux Impact mail server into thinking it was from NameCheap. The email was from an altogether different domain, with valid DKIM, SPF, and DMARC. While this does present a giveaway to eagle-eyed recipients, such as this writer, it practically guarantees entry into the main inbox.
We have a few domains due for renewal soon, and don't have automatic payments set up. All good so far.
The text seemed to be legit, was written in good English, and we suspect it was copied directly from a genuine NameCheap email.
There were links to update credit card details, to log into our account, or to contact customer support.
Overall, it was a good attempt, and we'd give it a five out of 10.
What gives a scam email away?
While this email was a solid effort, there were a few giveaways.
The first was that the title (not the subject) of the email was "Hosting Auto-Renew Failed." We don't have hosting with NameCheap. Although NameCheap hosting is a bargain, a little more research would have told the attacker that we actually host this site on GitHub pages.
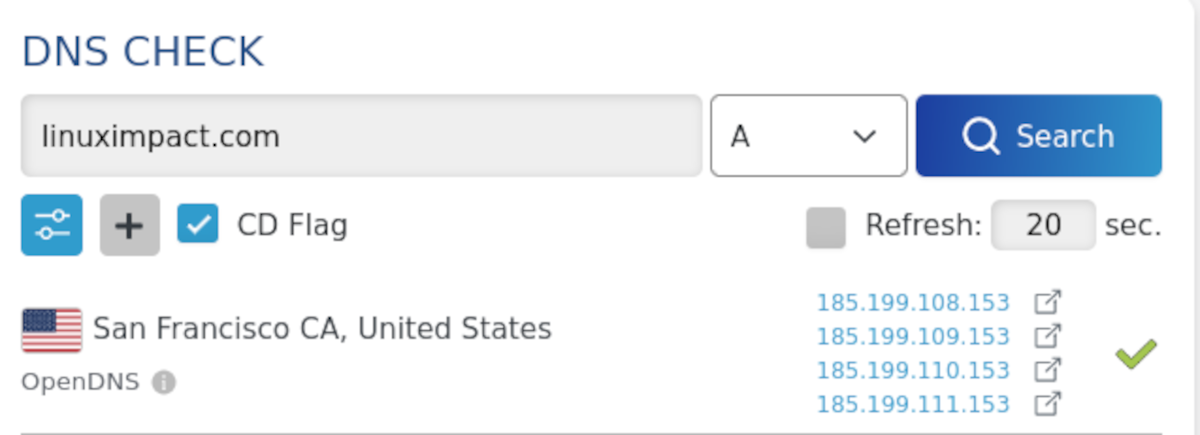
A further A record DNS check would have revealed IP addresses that are assigned to GitHub. Armed with this knowledge, the attacker could have crafted a different title that could, perhaps, have fooled us.
The next giveaway is the To field. The email was addressed to info@linuximpact.com. This isn't an actual address we use to register domain names, and came to us via catch-all forwarding. It's a good guess, but no, that email doesn't exist.
We have our webmail client set to not automatically download images. The reason for this is that if an image displays in your browser or email client, it has to be downloaded from a remote source, and it's possible for an attacker to monitor this, and know if a particular email has been opened. This can tell them that the email address is monitored and in use. That information is valuable on its own, and can make you the target of future attacks.
We do, however, get to see the source of the images that would be displayed if we allowed it.
Typically, images embedded in Namecheap emails are hosted at mktg.namecheap.com. Images in the scam email were from a googleusercontent CDN, and came with a long unique identifier - a dead giveaway.
Lastly, there's the fact that all the links - and the sender email are from a defunct WordPress site, with some shiny new subdomains set up expressly to catch the unwary. Of course, you won't easily be able to tell this if you're reading on mobile. You'll need to get to a desktop and hover your mouse over each link to check.
What can an attacker do with a stolen ID
Had we clicked through to the fake NameCheap site and entered our genuine email address and password, the results could have been catastrophic, and it's entirely feasible that this website would have redirected to a malware-laden spoof page.
With the ability to set DNS records, it's also likely that the attacker would have spun up an email server, and used it send out malicious, yet legitimate-seeming emails to trick other users. Again, we have dozens of domains registered with NameCheap, so this would be a gift that kept on giving.
They would have also tried to use the email and password combos against other services to see what matched It's good practice to protect your inbox by spinning up multiple aliases, and creating seperate identities for each online service you use.
We're as careful as we can be with emails, and there's an element of luck involved, too. The best thing you can do is stay vigilant, keep images off, and check everything.